Our Approach
|
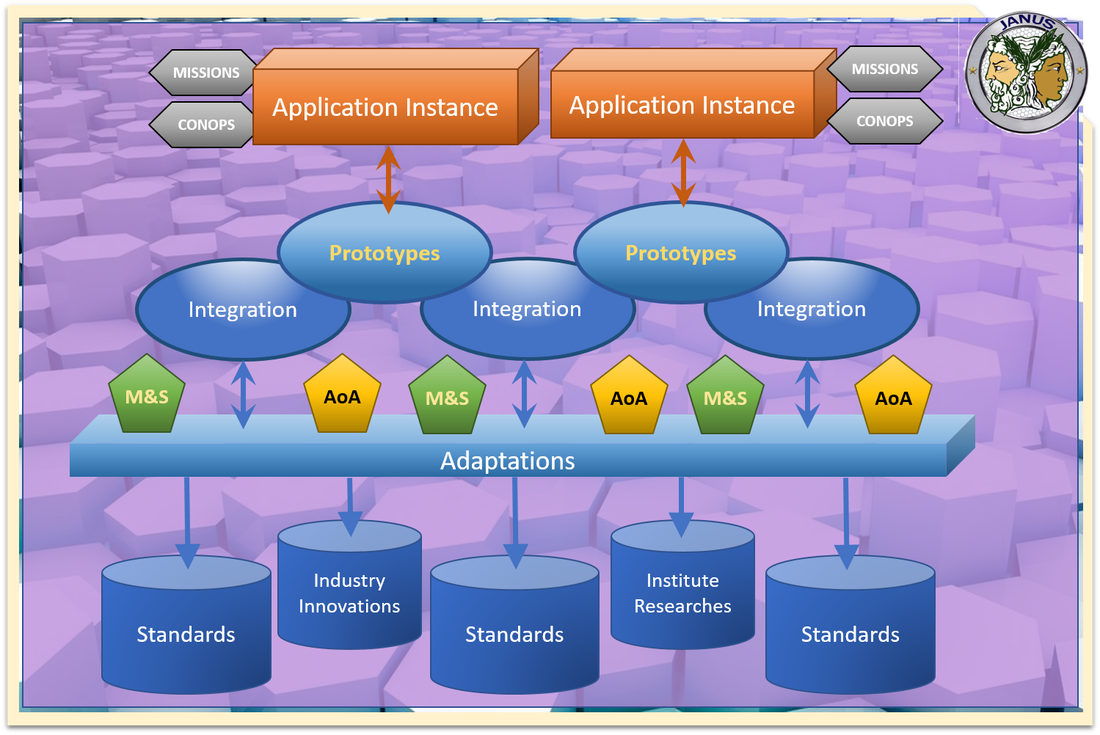
Janus Communications Research (JanusCore) follows the guidance from the DoD Modular Open Systems Approach (MOSA), which is an integrated business and technical strategy for assessment and implementation of open systems. The Janus Communications Architecture employs modular design tenets, uses industry and government standards to support key Interfaces for adaptation, and is subject to Validation and Verification to ensure the openness of its key interfaces. This approach helps to develop an affordable and flexible system for faster integrations and prototypes into fieldable application instances.
|
The five (5) MOSA principles are:
- (1) Establishes supportive requirements, business practices, and technology development, acquisition, test and evaluation, and product support strategies needed for effective development of open systems.
- (2) Employ Effective modular design adherence to four major modular design tenets:
- Cohesive (contain well-focused and well-defined functionality)
- Encapsulated (hide the internal workings of a module’s behavior and its data)
- Self-contained (do not constrain other modules)
- Highly binned (use broad modular definitions to enable commonality and reuse)
- (3) Designate Key Interfaces to address technological stability, high reliability, essential net-centricity, and vital interoperability.
- (4) Use Open Interface Standards that are well defined, mature, widely used, and readily available.
- (5) Openness of systems is verified, validated, and ensured through rigorous and well-established assessment mechanisms, well-defined interface control and management, and proactive conformance testing.
|
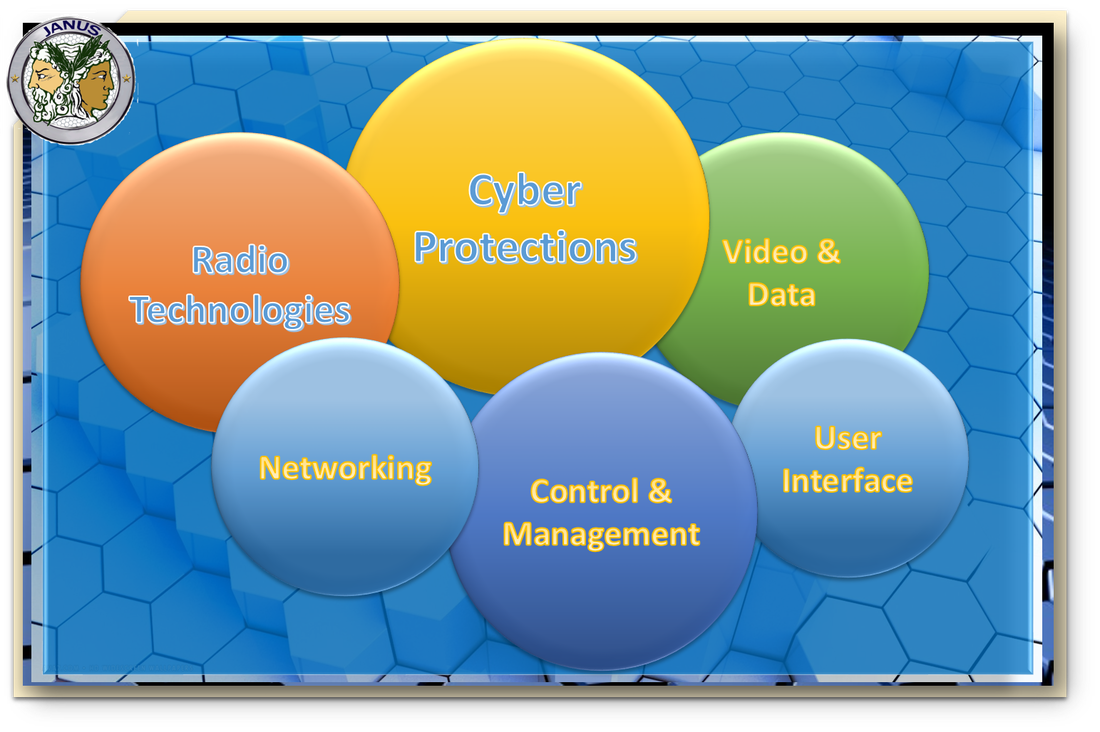
Our Specialties include the following domains:
|